Many Ghanaian business owners still view network security as a cost drain rather than a value generator. This mindset needs urgent transformation, especially given Ghana’s escalating cyber threat landscape.
Here is why: Ghana recorded 2,008 cyber incidents in the first half of 2025 alone—a staggering 52% surge from the entire previous year, according to the Ghana Cyber Security Authority.
These aren’t just statistics; they represent real businesses losing money, customers, and competitive positioning. The financial toll reached GHS 14.9 million in the first six months of 2025, primarily due to online fraud and unauthorized access.
Understanding the return on investment for network security companies in Ghana changes everything. It transforms security from a grudge purchase into a measurable business advantage.
This guide breaks down the ROI of hiring network security companies in Ghana, using real Ghana-specific data and proven formulas. You’ll discover practical assessment frameworks, authentic case studies, and actionable criteria for selecting security partners who actually deliver measurable value.
GET IN TOUCH
Protect your business with top-tier network security solutions
What Is Network Security & Why Does It Matter in Ghana
Network security is the set of controls that keeps your business network safe. It combines network defense strategies like firewall rules and segmentation. It also uses threat detection and response to spot attacks early. Strong endpoint protection, access controls, and encryption reduce exposure. When these layers work together, they protect data and uptime.
In Ghana, those technical safeguards translate into real business protection because today’s risk isn’t abstract—it’s measurable and rising. That’s why the ROI conversation starts with local exposure, then moves to prevention value:
- Ghana recorded 2,008 cyber incidents in H1 2025, a 52% jump from all of 2024.
- Reported cybercrime losses hit GHS 23.3 million in 2024 and GHS 14.9 million in H1 2025.
- With 4,753 DDoS attacks in H1 2024 and the region’s highest-volume attack at 314.25 Mbps, Ghana sits alongside Nigeria and Guinea as West Africa’s most targeted nations.
- CSA’s dark web monitoring revealed 35 Ghanaian organizations’ credentials actively traded on criminal marketplaces during early 2025.
Read more: Top 9 Network Security Companies in Ghana in 2026
How to Calculate Cybersecurity ROI in Ghana
Traditional ROI formulas don’t fit cybersecurity investments cleanly because security prevents losses rather than generating revenue. The standard equation—(Gain minus Cost) divided by Cost—works well for profit-driven initiatives but struggles with preventative spending. Security success means nothing bad happened, which creates measurement challenges.
That’s where Return on Security Investment (ROSI) comes in. ROSI adapts ROI thinking to measure what didn’t happen: breaches avoided, downtime prevented, penalties dodged. The formula looks like this: (Risk Mitigation Value minus Security Solution Cost) divided by Security Solution Cost.
Here’s a practical example: An Accra retail business faces a potential breach risk of GHS 500,000 based on customer data volume. They invest GHS 80,000 annually in managed security services including firewall management and threat monitoring. Successfully preventing a breach retains GHS 420,000 in value. The ROSI calculation yields 425%—far exceeding typical business investments.
Beyond formulas, key metrics worth tracking include:
- Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) for measuring incident handling speed
- Compliance penalty avoidance from Ghana’s Cybersecurity Act and Bank of Ghana directives
- Customer retention rates following security upgrades in trust-sensitive sectors
The challenge lies in valuing what didn’t occur—breaches stopped, downtime avoided, customers kept.
Read more: 5 Ways Software Companies in Ghana Protect Your Business from Data Breaches
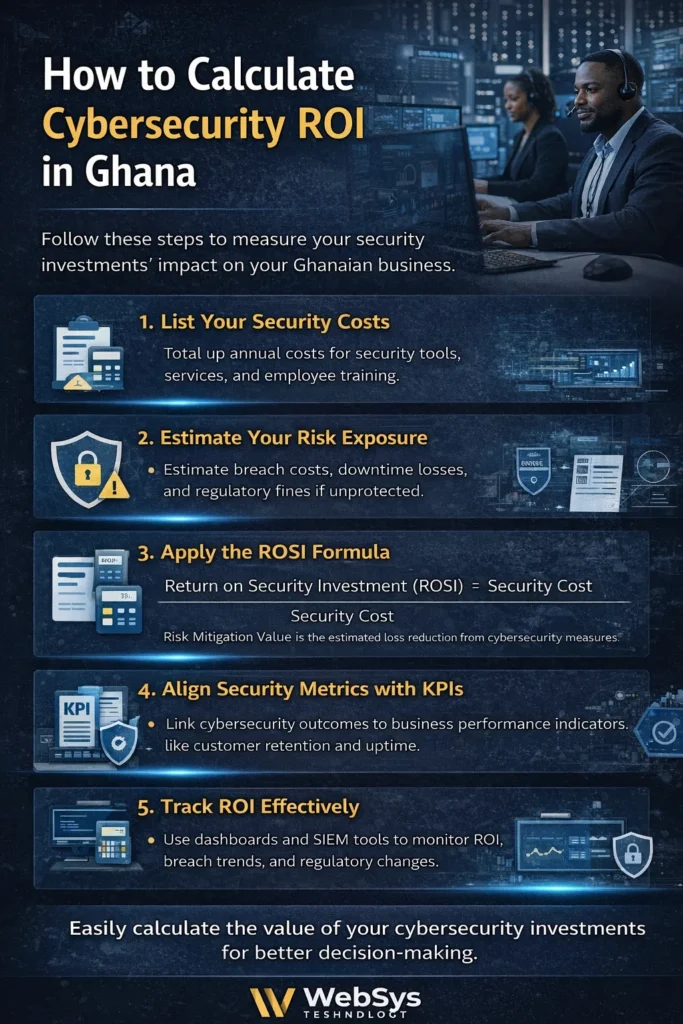
Practical Steps to Assess Network Security ROI for Your Ghanaian Business
Measuring the return on investment of network security in Ghana becomes much easier when you break it into structured steps that link real costs, real risks, and real business outcomes. Instead of guessing, you build a clear picture of how cybersecurity services protect revenue, reduce losses, and support long‑term growth.
1. List All Your Security Costs Clearly
Start by capturing every direct and indirect cost tied to protecting your network over a full year. This gives you a clean baseline before you calculate any ROI.
Include items such as:
- Licenses for antivirus, firewalls, VPN, endpoint protection, and SIEM systems
- Fees for managed security service providers and incident response retainers
- Salaries or partial salaries of internal staff handling cybersecurity work
- Security awareness training, certifications, and external security audits
Once you estimate the total annual cost, you have the “investment” side of your ROI equation.
2. Quantify Your Cyber Risk Exposure
Next, estimate the financial damage a serious incident could cause your Ghanaian business if no additional security measures were in place. Ghana lost GHS 23.3 million to cybercrime in 2024 and GHS 14.9 million in the first half of 2025, underscoring how quickly losses accumulate across sectors.
Consider these components:
- Direct breach costs: forensic investigations, legal fees, customer notification, and potential compensation
- Downtime impact: revenue lost per hour or day when systems, ATMs, e‑commerce, or mobile money channels are offline
- Regulatory penalties: potential fines linked to Ghana’s Cybersecurity Act and Bank of Ghana directives for non‑compliance
- Customer churn and reputational damage: clients who leave after incidents, especially in banking and digital payments
This combined figure represents your “exposure” if defences fail or remain weak.
3. Apply a ROSI‑Style Calculation
Return on Security Investment focuses on losses avoided rather than extra revenue created. A simple working formula is:
- ROSI = (Risk Mitigation Value − Security Cost) ÷ Security Cost
Risk mitigation value is the portion of your estimated exposure that robust cybersecurity can realistically reduce. For example, if your total potential loss is GHS 1 million and you conservatively believe current controls cut that risk by 60%, then the mitigation value is GHS 600,000. If you spent GHS 150,000 on security, ROSI becomes (600,000 − 150,000) ÷ 150,000 = 300%.
4. Connect Security to Business KPIs
Pure financial modelling isn’t enough on its own, so you also need to link security outcomes to business metrics your leadership already tracks.
Useful KPIs include:
- Reduction in incidents, successful phishing attempts, and malware infections after new controls are deployed
- Improved uptime across banking apps, e‑commerce sites, or internal systems that drive daily revenue
- Higher customer retention or lower churn after visible security improvements and compliance milestones
This alignment shows that network security is supporting sales, service quality, and long‑term loyalty rather than sitting in isolation within IT.
5. Use Dashboards and Regular Reviews
Finally, bring everything together with simple dashboards that track both technical and financial indicators over time. Many SIEM and security monitoring tools now offer reporting that Ghanaian SMEs and enterprises can use without large teams or complex setups.
To keep ROI accurate and current:
- Review incident statistics and response times every quarter
- Compare projected breach losses against actual events and near‑misses
- Adjust investments when cybercrime in Ghana spikes or new regulations tighten requirements
This ongoing evaluation helps you justify budgets confidently while proving that every cedi spent on network security supports resilience, compliance, and growth in Ghana’s fast‑moving digital economy.
Read more: Top Mistakes Businesses Make When Hiring Software Companies in Ghana

Core Elements of ROI for Hiring Network Security Firms
Network security companies in Ghana deliver returns ranging from immediate, quantifiable savings to long-term strategic advantages. Understanding both tangible and intangible benefits enables comprehensive ROI calculation.
Tangible ROI: Direct Financial Impact
Preventing security breaches generates the most obvious financial returns by avoiding catastrophic costs. The average data breach in Africa costs $3.2 million according to global benchmarks, though Ghana-specific incidents vary by organization size and sector. Financial institutions face particularly severe exposure, with serious breaches potentially costing GHS 2-5 million, including legal fees, regulatory fines, and forensic investigations.
A ransomware attack on a Ghanaian financial institution in 2024 disrupted critical services and resulted in $120,000 theft. The attackers encrypted 100 TB of data, of which authorities recovered only 30 TB despite specialized decryption tools. The full impact—including system rebuilding, customer notification, regulatory reporting, and reputational damage—multiplied the direct theft amount several times over.
Reducing downtime with proactive security delivers measurable productivity gains and revenue protection. Ransomware incidents can paralyze operations for days or weeks while IT teams attempt recovery. Managed security service providers cut incident response times from days to hours through 24/7 monitoring and established response protocols. Republic Bank Ghana achieved a 90% reduction in resolution times after implementing comprehensive security management, resolving critical issues in 2-3 hours, down from 2-3 days previously.
Optimized IT budget allocation represents another tangible benefit often overlooked in initial calculations. Engaging managed security service providers eliminates redundant security tool purchases and reduces staff time spent firefighting. Predictable monthly service costs replace unpredictable emergency breach spending. Staff productivity redirects from crisis management to innovation and growth initiatives.
Intangible ROI: Strategic Business Value
Enhanced customer trust and loyalty through secure operations creates competitive differentiation increasingly crucial in Ghana’s digital economy. Research shows 67% of consumers globally abandon brands following data breaches. In Ghana’s competitive fintech and mobile money sectors, security becomes a primary selection criterion for discerning customers.
Network security compliance with Ghana’s regulatory framework delivers multiple strategic advantages. The Cybersecurity Act (Act 1038) mandates protection standards across sectors. The Bank of Ghana’s 2018 Cyber and Information Security Directive requires financial institutions to establish governance structures and appoint Chief Information Security Officers. Proactive compliance avoids penalties while streamlining audit processes and regulatory interactions.
Market positioning advantages flow from recognized security certifications and demonstrated protection capabilities. Enterprise clients increasingly demand assurances of security before signing contracts or sharing sensitive data. International partnerships often require ISO 27001 certification or equivalent security standards. Investment in professional security services opens doors to higher-value clients and partnerships previously inaccessible.
Protecting intellectual property and competitive intelligence represents immeasurable value until a breach occurs. Product development data, customer insights, pricing strategies, and operational methods constitute core business assets. Once leaked to competitors or public forums, these advantages vanish permanently.
Read more: Why Partnering with Software Companies in Ghana is More Cost-Effective Than Outsourcing
How Ghana Businesses Specifically Benefit
Ghana’s economic sectors face distinct cybersecurity challenges requiring tailored approaches with sector-specific ROI characteristics.
- SMEs gain disproportionate protection because smaller businesses typically lack recovery resources following major incidents. The GHS 14.9 million in cybercrime losses in the first half of 2025 hit SMEs particularly hard, as they rarely maintain insurance or reserve funds for cyber incidents. A single significant breach can mean permanent closure for businesses operating on thin margins. Affordable managed security service providers democratize enterprise-grade protection previously accessible only to large corporations. Cloud-based security monitoring and outsourced expertise level the playing field, giving SMEs the same threat intelligence capabilities as multinational corporations.
- Financial services operate under intense regulatory scrutiny, where security investments deliver multiple simultaneous returns. The Bank of Ghana’s 2018 Cyber and Information Security Directive mandates specific controls, governance structures, and the appointment of a CISO. A Ghanaian bank facing regulatory deadlines turned to Managed Detection and Response services, meeting compliance requirements within weeks rather than months. They gained 24/7 threat monitoring without a lengthy in-house Security Operations Center buildout while avoiding potential regulatory penalties.
- Telecommunications and digital payment platforms face critical infrastructure vulnerabilities that directly impact revenue. Ghana’s computer-related services sector absorbed 2,759 DDoS attacks in the first half of 2024 alone. Service availability directly correlates with revenue for telcos and mobile money operators—minutes of downtime translate into thousands of lost transactions.
- Legislative support creates compliance imperatives across all sectors. Ghana’s Cybersecurity Act establishes accountability frameworks with legal consequences for inadequate protection. The Cyber Security Authority’s licensing regime registered over 1,200 service providers by the end of 2023, professionalizing the marketplace. Security investments simultaneously meet regulatory requirements and deliver business protection, creating dual-benefit ROI.
Proven ROI: Case Studies of Network Security Success in Ghana
When you look at real organizations in Ghana, the business value of strong network security becomes very concrete. These examples show how structured investments translate into faster operations, stronger resilience, and measurable financial protection.
National Cyber Resilience: Ghana’s Global Leap
Ghana’s cybersecurity journey has become a reference point for other African countries, thanks to coordinated public and private investment. A World Bank case study highlights how the country strengthened its cyber resilience over just a few years.
Key national‑level outcomes include:
- Ghana moved from 89th to 43rd place globally in the ITU Global Cybersecurity Index, a jump of 46 positions in three years.
- The country became one of only seven African nations ranked in the global top 50 for cybersecurity readiness.
- Sectoral Computer Emergency Response Teams (CERTs) were established for banking, government, telecoms, and national security, giving Ghana an incident response capability that most African states still lack.
These improvements didn’t just boost rankings. They attracted international partnerships, enabled Ghana to host the first Global Cyber Capacity Building Conference in 2023, and positioned the country as a regional hub for cyber expertise.
Republic Bank Ghana: Faster Resolution, Better Service
At the enterprise level, Republic Bank Ghana provides a clear example of how structured IT and security management pay off operationally. By implementing an integrated IT service management platform with strong security processes, the bank achieved significant gains.
Documented results include:
- Around 90% reduction in incident resolution times, cutting critical issue handling from 2–3 days to about 2–3 hours.
- Expansion from 50 to 100 administrators using the platform across IT, banking operations, and risk management teams, doubling adoption and collaboration.
- Automation of ticket routing and approvals, which reduced manual workload and freed staff to focus on higher‑value tasks.
These outcomes translate directly into ROI through reduced downtime, fewer service disruptions, and better customer experience for banking clients in Ghana.
Large Financial Institution: Endpoint Protection at Scale
A leading financial institution in Ghana with more than 120 branches rolled out ESET Endpoint Protection Advanced to secure its distributed network. The organization needed to balance performance, bandwidth efficiency, and strong threat detection and response.
The case study reports that:
- The deployment improved bandwidth usage across the branch network while maintaining robust protection against malware and zero‑day threats.
- The institution cited better overall value when comparing ESET’s features, performance, and support with alternative solutions considered.
For a branch‑heavy financial institution, this combination of protection and performance means fewer disruptions, lower operational risk, and sustained customer trust in digital and in‑branch services.
CERT‑GH and Sectoral CERTs: Shared Infrastructure, Shared ROI
Ghana’s national and sectoral CERT structures also deliver collective ROI by lowering the average risk and response cost for individual organizations. CERT‑GH and sector‑specific teams in banking and telecoms provide:
- Real‑time threat intelligence sharing and coordinated response to major incidents.
- Access to global monitoring networks helps local operators detect and contain advanced threats faster.
Instead of every organization building isolated capabilities, this shared infrastructure spreads costs while raising the country’s overall defensive baseline, a powerful form of security ROI at the ecosystem level.
Key Pitfalls in Network Security Investment and How to Avoid Them
Even when budgets are approved, many Ghanaian businesses still fail to get full value from their network security spend because of a few recurring mistakes. Understanding these pitfalls helps you turn cybersecurity into a true business asset rather than a confusing cost line.
1. Looking Only at License Costs
Many teams focus on the price of firewalls or antivirus software and forget everything else.
- They ignore the time required for implementation, integration, and ongoing management.
- Training, security audits, and renewals are excluded from the numbers.
To avoid this, calculate the total cost of ownership over three to five years, including tools, people, and processes.
2. Underestimating the True Cost of a Breach
Some leaders only count immediate cash losses and skip wider damage.
- Brand damage and customer churn can multiply direct losses several times.
- In Ghana’s close‑knit markets, reputation issues travel fast and last long.
Use conservative multipliers (3–5x the direct loss) when modelling breach impact to keep your ROI estimates realistic.
3. Treating Compliance as “Paperwork”, Not Money
Regulations like Ghana’s Cybersecurity Act and Bank of Ghana directives carry real financial teeth.
- Non‑compliance can trigger fines, license issues, and intense scrutiny.
- Fixing problems under regulatory pressure usually costs more and causes disruption.
Position compliance as a measurable risk‑reduction tool: compare the cost of meeting requirements against potential penalties and operational restrictions you avoid.
Key Criteria for Picking the Right Network Security Firm in Ghana
Your security ROI depends entirely on choosing providers who understand Ghana’s threat landscape while delivering measurable business outcomes. The wrong partner drains budgets without protecting what matters most.
Check Certifications and Official Registration
Look for professionals holding the Certified Information Systems Security Professional (CISSP), Certified Ethical Hacker (CEH), or CompTIA Security+ credentials, which validate technical competency. ISO 27001 auditor qualifications show they can implement internationally recognized standards.
Verify registration with the Cyber Security Authority of Ghana, which maintains a registry of over 1,200 licensed service providers, establishments, and professionals. Registration indicates basic compliance with national standards and regulatory accountability.
Evaluate Industry Experience and Local Presence
Sector-specific experience matters significantly when assessing potential partners. Financial institutions need providers familiar with Bank of Ghana directives and banking threat patterns. Telecommunications companies require DDoS mitigation expertise, as Ghana’s computer services sector experienced 2,759 attacks in H1 2024 alone.
Ghana-based teams respond faster to incidents and understand regional threat actors better than offshore-only providers. They navigate relationships with the Ghana National Communications Authority and CSA more effectively.
Review Service Portfolio Depth
Managed Detection and Response capabilities provide 24/7 monitoring essential for organizations lacking in-house Security Operations Centers. Ask about clearly defined service level agreements specifying response times for different incident severities.
Core services should include:
- Vulnerability assessment and penetration testing to identify weaknesses proactively
- Incident response with documented procedures and average containment times
- Compliance consulting for navigating Ghana’s Cybersecurity Act and Bank of Ghana directives
- Security awareness training programs that reduce human error vulnerabilities
Ask Critical Pre-Contract Questions
Request Ghana-specific client references you can contact directly to verify claimed capabilities and service quality. Ask about average incident response times for local clients, not generic global averages that ignore infrastructure constraints.
Understand which SIEM systems, firewall technology, and intrusion detection systems they deploy. Technology choices impact integration with your existing infrastructure and long-term supportability.
Inquire about staff retention rates—high turnover disrupts the continuity essential for effective security partnerships. Learn how they handle regulatory reporting requirements to CSA and sector regulators to reduce your administrative burden.
Conclusion
Network security companies in Ghana transform cybersecurity from a defensive expense into measurable business growth. ROSI calculations prove every cedi invested prevents losses while enabling revenue opportunities through certifications and customer trust. Ghana’s 2,008 cyber incidents in six months show threats accelerating faster than most businesses prepare for.
From Republic Bank’s 90% faster incident resolution to Ghana’s 46-position leap in its cybersecurity ranking, real organizations demonstrate clear returns. Security maturity now separates growing digital businesses from those struggling to survive cyber disruptions.
Ready to see your actual security ROI? WebSys Technology delivers measurable network security outcomes for Ghanaian businesses through comprehensive threat detection, managed services, and compliance expertise. Our local specialists design protection that aligns with your operations and regulatory needs while proving returns through reduced incidents and operational gains.
Contact WebSys Technology today for your complimentary ROI assessment. Turn cybersecurity spending into a strategic advantage before threats hit your bottom line.
GET IN TOUCH

